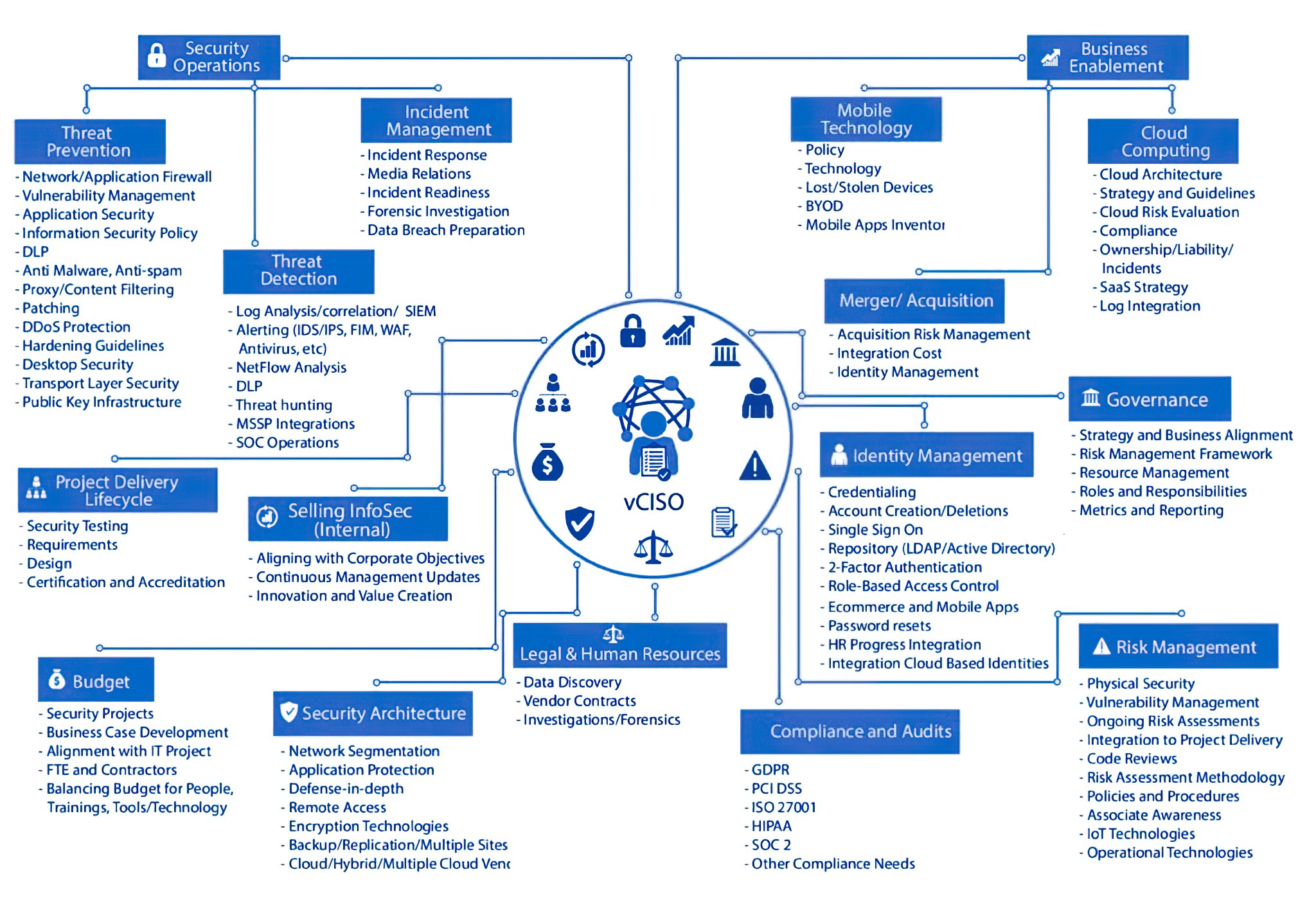
Our Approach
Approach we follow

Evaluate
Assess the current security posture and controls of the organization and understand their pain points.
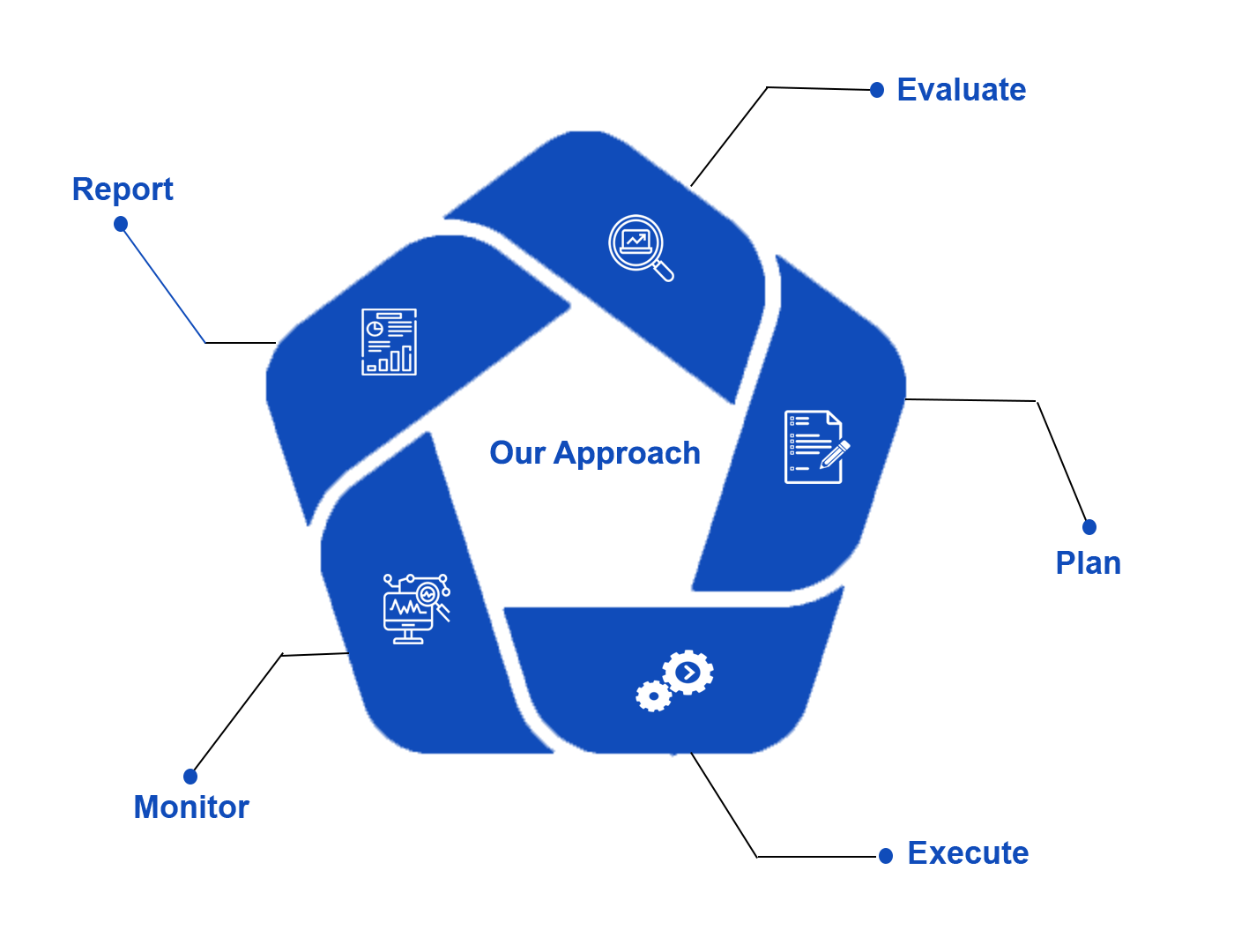

Plan
Define security road map and objective that is inline with the organization business objective.
Execute
Identify appropriate security controls and oversee implementation of the security controls.


Monitoring
Continuously monitor the effectiveness and adherence of the implemented security control.
Report
Develop and provide metrics report to the senior management.