Our Approach
Approach we follow
Planning & Reconnaissance
We plan the execution of the security testing activities and determine the tools required for a successful execution. Required information is gathered before execution of the assessment.
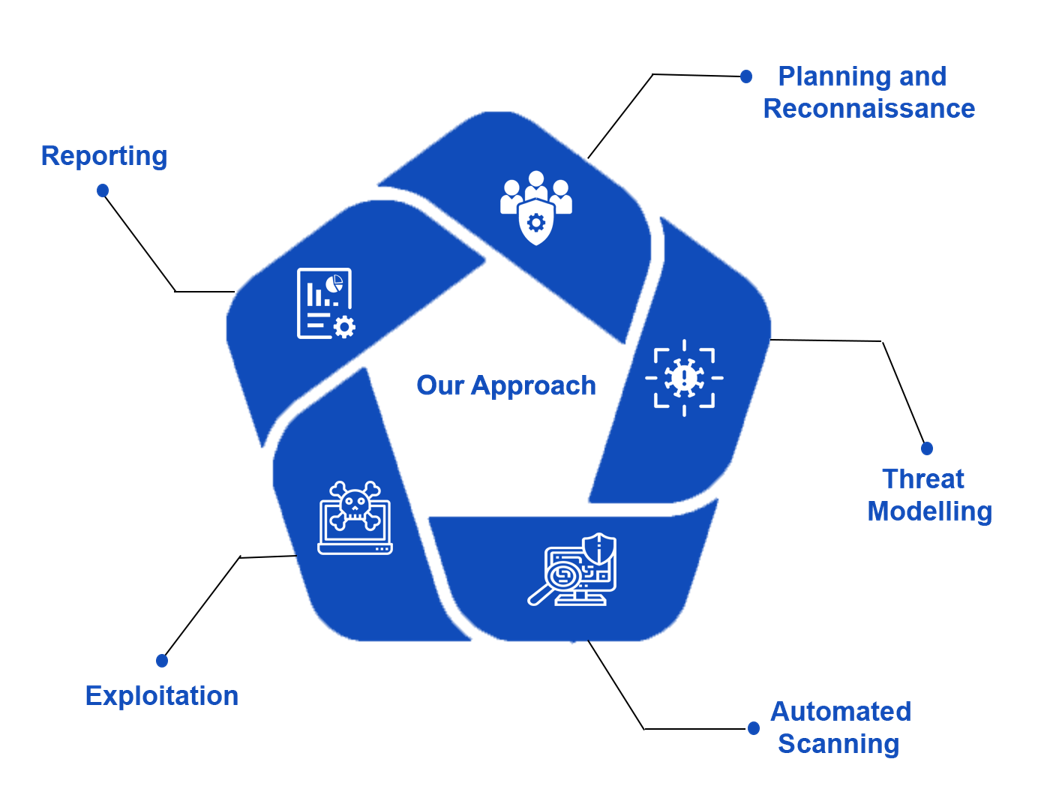
Threat Modeling
We model the threats of your mobile app and business. We help you with a road map to address your threats.
Automated Scanning
Assessment scope is determined and reviewed with the client and the expectations of the engagement are detailed and agreed.
Exploitation
Verify the exploitability of the identified vulnerabilities by performing manual analysis and penetrate the application through payload injection.
Reporting
On completion of the technical assessment activities we will provide an assessment report detailing the findings and recommendations for fixing the same.