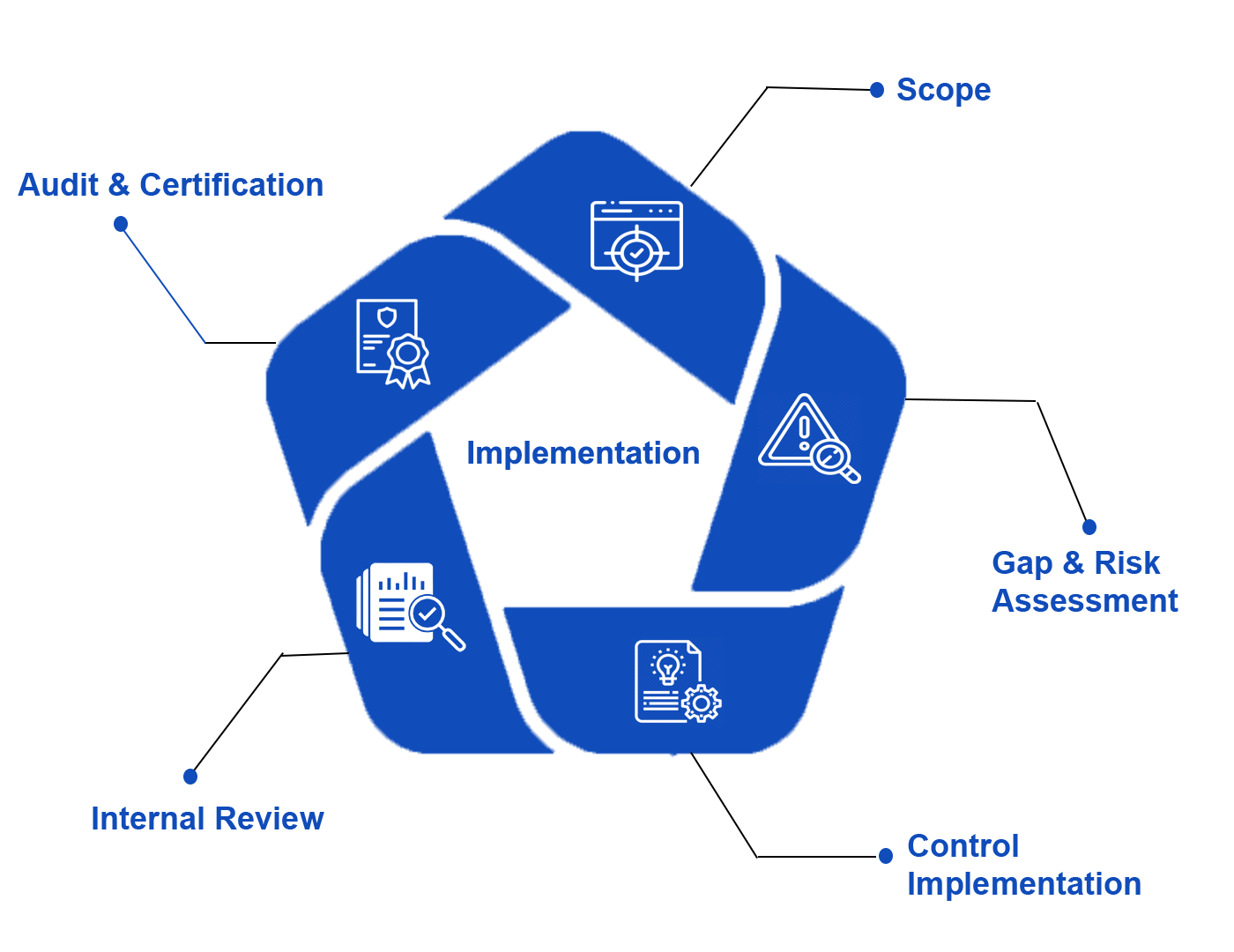
Our GRC Services
Audit Service
We help organizations with our audit service to evaluate the effectiveness of the implemented GRC controls.

Define
Define the scope of the audit inline with the framework / standard’s certification scope.
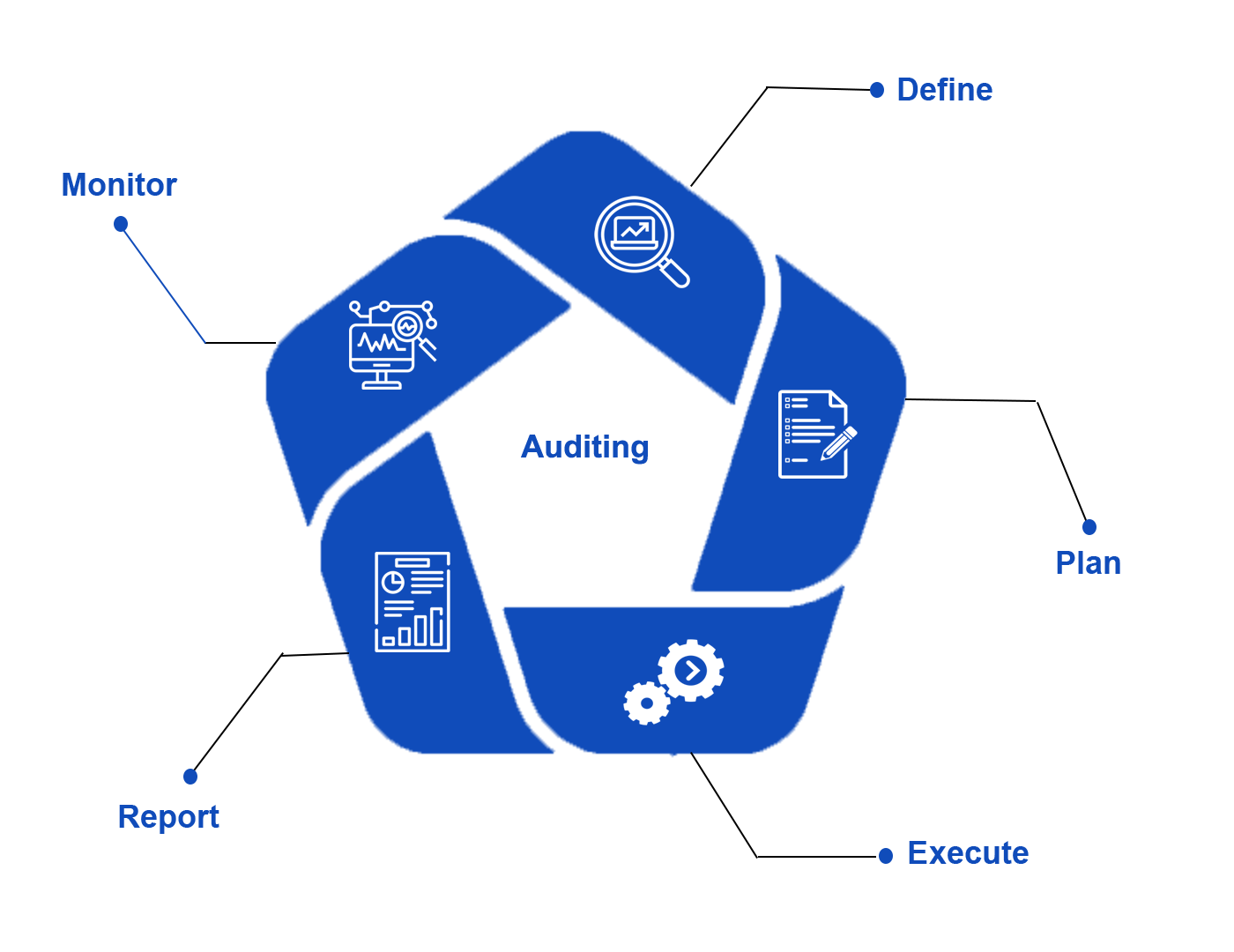

Plan
Define project plan which involves generating an framework audit work plan, in which the timing and resourcing of the audit is agreed with management.
Execute
Organization’s policy, procedure and implemented controls are reviewed to identify the effectiveness of the control definitions and its implementation.


Report
A detailed audit report shall be prepared and presented to the management and the required staff for concurrence and further action.
Monitor
The results from the fieldwork and the evidences were analysed for its relevance and appropriate corrective actions were identified for reporting.